Steven L. Basha, Esq.
November 19, 2017
Information:
Quick Glance:
Links: ADJ 243 Homeland Security and the Law: Notes 2 |
|||
|---|---|---|---|
Home Page // Assignments Page // Notes 1 // Notes 2 // Notes 3 // Notes 4 // Exam Page // Books // Paper // Articles |
|||
| Date: | Links: | ||
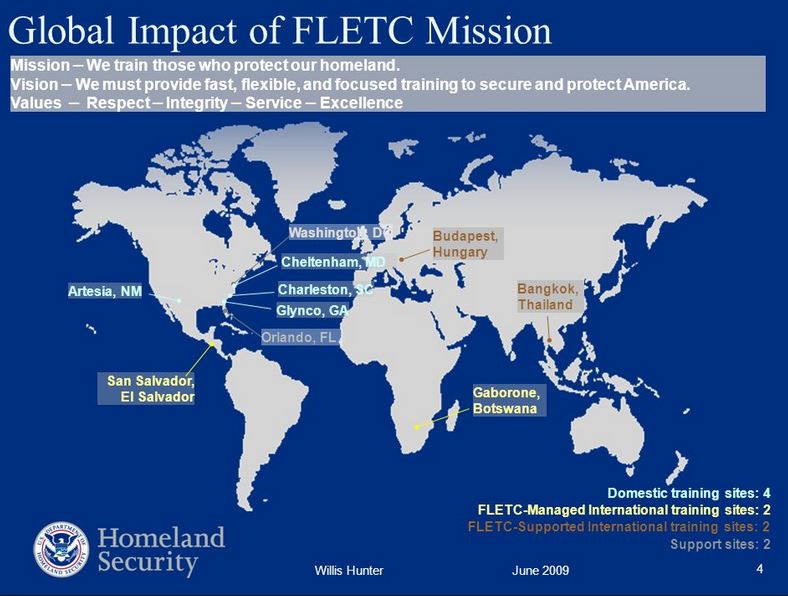
| Chapter 4 | October 1, 2017 | Training
National Domestic Preparedness Consortium: The NDPC is a DHS/FEMA training partner providing high-quality training to emergency responders throughout the United States and its territories. The NDPC is a National Homeland Security Training Asset.| PDF
The New Mexico Tech school offers FEMA training at its Energetic Materials Research and Testing Center. It is located in Socorro, NM. It is near White Sands Missle Range.
These sites will help law enforcement to react to incidents in Content for class "white_outline" Goes Here
a logical way with the proper training. Some classes are given in Spanish.
The Federal Law Enforcement Training Center is located several locations and provide current training for law enforcement.
The Washington Operation is located in the Nation's Capital.
National Preparedness Network (PREPnet)--Could not find a specific Website for this. This is a public first responders programming schedule.
National Fire Academy--The National Fire Academy (NFA) works to enhance the ability of fire and emergency services and allied professionals to deal more effectively with fire and related emergencies. Free training courses and programs are delivered at our campus in Emmitsburg, Maryland.
Noble Training Center--Hospital based training
The Emergency Management Institute is effective training working together in trainings. Catalog And is located in Emmitsburg, MD at the former Civil Defense Staff College.
The Department of Homeland Security's National Integration Center is responsible for managing the implementation and administration of the National Incident Management System (NIMS). ... The goal, and typical result of NIMS, is a coordinated, faster, and more effective resolution
The Comprehensive HAZMAT Emergency Response - Capability Assessment Program (CHER-CAP) is to expand the scope of the highly successful community-based initiative. It is a resource to prepare for Haz materials incidents.
The National Preparedness Goal calls for a secure and resilient nation with the capabilities required across the whole community to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk.
Post-Katrina Emergency Management Reform Act of 2006 (PKEMRA). PKEMRA significantly reorganized FEMA, provided it substantial new authority to remedy gaps in response, and included a more robust preparedness mission for FEMA.
Citizen Corps--The mission of Citizen Corps is to harness the power of every individual through education, training, and volunteer service to make communities safer, stronger, and better prepared to respond to the threats of terrorism, crime, public health issues, and disasters of all kinds.
TOPOFF means a high level executive at Homeland Security.
The Assistance to Firefighters Grant Program
Operation Stonegarden is a federal grant program administered by the Federal Emergency Management Agency (FEMA), a component of the Department of Homeland Security, as part of the State Homeland Security Grant Program. Stonegarden provides funding to state, local, and tribal law enforcement agencies to enhance their capabilities "to jointly secure U.S. borders and territories."
Fiscal Year 2017 Homeland Security Grant Program: Total Funding Available in Fiscal Year (FY) 2017: $402,000,000 PURPOSE The SHSP assists state, tribal and local preparedness activities that address high-priority preparedness gaps across all core capabilities and mission areas that support terrorism preparedness. All supported investments are based on capability targets and gaps identified during the Threat and Hazard Identification and Risk Assessment (THIRA) process, and assessed in the State Preparedness Report (SPR).
You will find a compilation of college courses on hazards, disasters and emergency management subjects provided by various colleges. |
|
| Week 2 | October 7, 2017 |
An Act is is a compilation of laws under one act on the same subject--they are grouped together.
The FBI is under the Department of Justice. The Treasury has the IRS. The Law Enforcement Agency (LEA) has the DEA, USMS (marshall service), and ATFE. DHS has USCG, ICE, CBP, and USSS. The Intelligence Agency (IA) has the CIA, DIA, and NSA.
Section 215: Access to records and other items under FISA: This section is commonly referred to as the "library records" provision[29] because of the wide range of personal material that can be investigated.
For sneak and peek warrants, now by statute so you can't do it and then not have it eventually revealed.
A sneak and peek search warrant (officially called a Delayed Notice Warrant and also called a covert entry search warrant or a surreptitious entry search warrant) is a search warrant authorizing the law enforcement officers executing it to effect physical entry into private premises without the owner's or the occupant's permission or knowledge and to clandestinely search the premises; usually, such entry requires a stealthy breaking and entering. Under the USA PATRIOT Act signed into law during the 107th United States Congress on October 26, 2001, sneak and peek warrants for the first time in United States history were used as standard procedure in investigations.
With the National Security Office, Advisors and staff reach out to agencies and get input. It has a homeland security security advisor also.
He commented that security gaurds must be careful when responding to an incident that has an active shooter because security may be walking into a booby trap.
Identify risk of something bad....What risk do you want to minimize?
On a basic level, DHS wants to minimize risk, manage risk. What is done is to manage risk in a mathematical way/scentific way methodology would be the risk management that is used.
Since 1789, Customs have been around in the U.S. What is brought in and what is taken out. The primary mission is terrorist and terrorist implements. Taxes are some times used in trade.
CBP is one of the largest law enforcement agencies in the United States. It has a workforce of more than 45,600 sworn federal agents and officers. It has its headquarters in Washington, D.C.
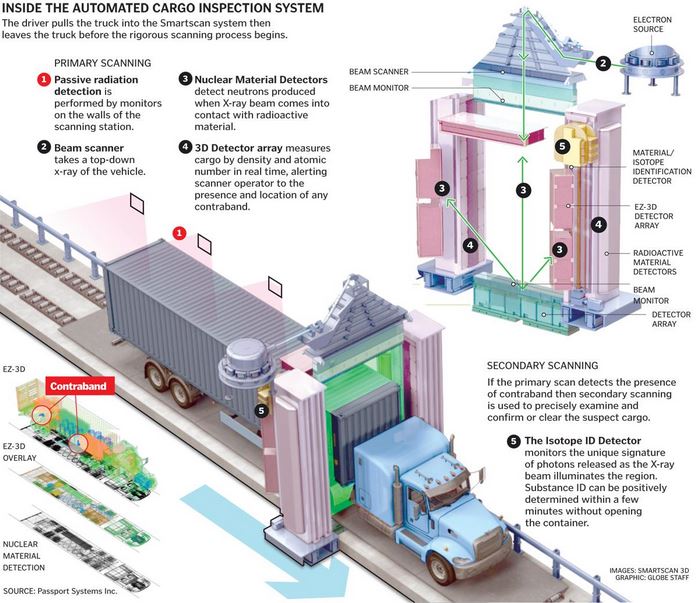
Read image above to figure out what is done to check trucks and I guess cargo.
ACE and Automated Systems ACE Logo The Automated Commercial Environment (ACE) is the primary system through which the trade community reports imports and exports and the government determines admissibility.
The CBP takes in all types of information such as databases, public info, other agencies, and determine what need to be inspected. What is the risk. A score is given based on the information. It is not an algorithm but are rules given. Score is 0 to 100% risk.
What is a Customs broker? Customs brokers are private individuals, partnerships, associations or corporations licensed, regulated and empowered by U.S. Customs and Border Protection (CBP) to assist importers and exporters in meeting Federal requirements governing imports and exports. Brokers submit necessary information and appropriate payments to CBP on behalf of their clients and charge them a fee for this service.
On average, the typical shipworker is a male Filipino; Filipinos make up one third of all shipworkers, and men constitute 98 percent of the work force. It is said that 90% of merchandise come to 20 ports in the United States.
Cargo planes bomb plot: Explosives were found in inkjet cartridges on an airplace from Yemen bound for the United States. Found in toner cartridges. WOW!
CARVER is an acronym that stands for Criticality, Accessibility, Recuperability, Vulnerability, Effect and Recognizability and is a system to identify and rank specific targets so that attack resources can be efficiently used. CARVER can be used from an offensive (what to attack) or defensive (what to protect) perspective. Also known as reverse engineering tool, assessment tool that was used by the green beret.
Criticality is how critical is it?, Accessibility is Can you physically go to?, Recuperability is Can you recover fast?, Vulnerability is how easy?, Effect is What do you use? and Recognizability is how easy to see? -- 7th is shock is the combined measure of the health, psychological, and collateral national economic impacts
He discussed that in WW1 trench warfare was used as a means to fight wars and thus there was a lessons learned on what to do in the next war. For example, The French used the Maginot Line which was a very elaborate line of military built on the eastern border of France to defend against an attack from Germany in 1928-39.
So, is the TSA using outdated technology? Is there a new attack metric that will be used or what about shoe bombs, is that dated technoloy? What method of attacks will be used in the future?
Indictments and convictions for possession and use of WMD such as truck bombs, pipe bombs, shoe bombs, and cactus needles coated with a biological toxin have been obtained under 18 USC 2332a.
18 U.S. Code § 2331 b : (1) the term "international terrorism" means activities that— (A) involve violent acts or acts dangerous to human life that are a violation of the criminal laws of the United States or of any State, or that would be a criminal violation if committed within the jurisdiction of the United States or of any State; (B) appear to be intended— (i) to intimidate or coerce a civilian population; (ii) to influence the policy of a government by intimidation or coercion; or (iii) to affect the conduct of a government by mass destruction, assassination, or kidnapping; and
A pipe bomb is an improvised explosive device, which uses a tightly sealed section of pipe filled with an explosive material. The containment provided by the pipe means that simple low explosives can be used to produce a relatively large explosion, and the fragmentation of the pipe itself creates potentially lethal shrapnel.
There are conflicting reports on what countries have nuclear bombs.
He said that 20 countries have a nuclear bomb. He mentioned South America, Isreal, and India. He also said Pakistan has a bomb.
He mentioned we should test in our homes for Radon which is a chemical element with symbol Rn and atomic number 86. It is a radioactive, colorless, odorless, tasteless noble gas. Atomic Isotopes and Medical Isotopes.
Ricin is a highly toxic, naturally occurring lectin produced in the seeds of the castor oil plant--castor beans.
The first wide scale use of chemical weapons was used in WW1 and these weapons are now outlawed.
Sarin is a colorless, odorless liquid, it is used as a chemical weapon due to its extreme potency as a nerve agent. Exposure is lethal even at very low concentrations
|
|
| Chapter 4b | Form I-94, the Arrival-Departure Record Card, is a form used by U.S. Customs and Border Protection (CBP) intended to keep track of the arrival and departure to/from the United States of people who are not United States citizens or lawful permanent residents
The Federal Protective Service (FPS) Mission Statement is to prevent, protect, respond to and recover from terrorism, criminal acts, and other hazards threatening the U.S. Government's critical infrastructure, services, and the people who provide or receive them.
The Homeland Infrastructure Threat and Risk Analysis Center (HITRAC) serves this national mission through its Homeland Security Risk Analysis Program, designed to fill the gap between the theory of risk management, and its successful application by public and private sector partners.
FDA Announces the Availability of "CARVER + Shock Vulnerability Assessment Tool" | Educational Materials | It appears the software has been taken off the Internet
The Sandia National Laboratories (SNL), managed and operated by the National Technology and Engineering Solutions of Sandia (a wholly owned subsidiary of Honeywell International), is one of three National Nuclear Security Administration research and development laboratories.
The November 2015 Paris attacks were a series of coordinated terrorist attacks that occurred on Friday 13 November 2015 in Paris, France. Deaths 137 (130 victims, 7 perpetrators)
Pipe bombs can be considered a WMD....
The Domestic Nuclear Detection Office (DNDO) is a jointly staffed office within the Department of Homeland Security. DNDO is the primary entity in the U.S. government for implementing domestic nuclear detection efforts for a managed and coordinated response to radiological and nuclear threats, as well as integration of federal nuclear forensics programs.
DHS Active Shooter Video
Force on Force (FOF) exercises are when DHS has a force attack thier facility to test if the security force is effective. Some attacks are commando style.
Radiological Assessment System for Consequence AnaLysis (RASCAL): The RASCAL code is a tool used by the Protective Measures Team in the U.S. Nuclear Regulatory Commission's (NRC's) Operations Center for making independent dose and consequence projections during radiological incidents and emergencies. Meetings
CDC emergency preparedness and response for dirty bombs. What is a dirty bomb? A dirty bomb is a mix of explosives, such as dynamite, with radioactive powder or pellets. When the dynamite or other explosives are set off, the blast carries radioactive material into the surrounding area.
What are the main dangers of a dirty bomb? The main danger from a dirty bomb is from the explosion, which can cause serious injuries and property damage. The radioactive materials used in a dirty bomb would probably not create enough radiation exposure to cause immediate serious illness, except to those people who are very close to the blast site. However, the radioactive dust and smoke spread farther away could be dangerous to health if it is inhaled. Because people cannot see, smell, feel, or taste radiation, you should take immediate steps to protect yourself and your loved ones.
Exercise conducted to test reaction to a disaster in real time to learn and see how effective it is.
A dirty bomb is not a "Weapon of Mass Destruction" but a "Weapon of Mass Disruption," where contamination and anxiety are the terrorists' major objectives.
In Kingston, NY there are soldiers at the 222nd Chemical Company. There are first responders there and they are a National Guard Unit.
Bioterrorism is terrorism involving the intentional release or dissemination of biological agents.
The DHS BioWatch Program's mission is to operate a nationwide, aerosol detection system providing early warning across all levels of government to support public health and emergency management communities to prepare for and respond to biological incidents.
Japanese Unit 731 Bioterrorism Anthrax
Russians had/has a large biologic warfare. ----------------------------------- Gruinard Island Anthrax Biological Warfare Experiment Great Britain 1942--Anthrax trials. Anthrax was dispersed on Gruinard Island where sheep roamed free. The Sheep died and the soil was impacted but later cleaned up.
Quick Facts
The Anthrax Vaccine Immunization Program (AVIP), is the name of the policy set forth by the U.S. federal government to immunize its military and certain civilian personnel with the BioThrax anthrax vaccine.
The impact of anthrax is both painful and extreme.
The Plague
The plague is also an infectious airborne disease that affects others who come in contact with its strain of bacteria too and you can be bitten by a fly and be contaminated.
Travelers Health Notices and these are from the CDC
Smallpox is considered the king of bioterrorism.
Smallpox is one of two infectious diseases to have been eradicated, the other being rinderpest, which was declared eradicated in 2011.
The United Nations online library headquartered in Geneva Switzerland and HERE
Tokyo subway terrorist attack using sarin gas.
Chemical weapons WW1 -- Although the use of toxic chemicals as weapons dates back thousands of years, the first large scale use of chemical weapons was during World War I. They used Chlorine Gas, Mustard Gas, etc. 1925 Geneva Convention to ban use of chemical warfare.
Movie Clip: WW1 Gas Attack
Some speculate that Syrians are using chemical weapons.
NIOSH Pocket Guide to Chemical Hazards
The by products of castor oil makes Ricin.
On October 15, 2003, an envelope with a threatening note and a sealed container was processed at a mail processing and distribution facility in Greenville, South Carolina. The note threatened to poison water supplies if demands were not met.
Sarin is a colorless, odorless liquid, it is used as a chemical weapon due to its extreme potency as a nerve agent. It is a preferred choice for terrorist due to its ease of delivery.
Most nerve agents started out being made for pesticides but the military became interested because of thier toxic nature.
Chemical Security Assessment Tool (CSAT) Personnel Surety Program: The Chemical Facility Anti-Terrorism Standards (CFATS) program fosters security at America's highest risk chemical facilities.
The Chemical Facility Anti-Terrorism Standards (CFATS) program identifies and regulates high-risk chemical facilities to ensure they have security measures in place to reduce the risks associated with these chemicals
Tabun is a man-made chemical warfare agent classified as a nerve agent. During WW2, this agent was potentially going to be used to kill Hitler. Below is some of the stockpile of the Americans.
VX is another nerve agent that is very powerful--potent.
Clothing of a contaminated purpose can release agents for 30 minutes after exposure.
Improvised explosive device (IED) weapons are explosive device fashioned and made not from conventional miliary methods.
A car bomb, or truck bomb, also known as a vehicle-borne improvised explosive device (VBIED), is an improvised explosive device placed inside a car or other vehicle and detonated.
USS Cole Bombed In Gulf Of Aden Yemen Oct 2000
US-Cert Security Publications-- These documents can help you with everything from setting up your first computer to understanding the nuances of emerging threats.
US-CERT strives for a safer, stronger Internet for all Americans by responding to major incidents, analyzing threats, and exchanging critical cybersecurity information with trusted partners around the world.
The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. The NVD is sponsored by the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) / United States Computer Emergency Readiness Team (US-CERT). For modified or updated entries, please visit the NVD, which contains historical vulnerability information.
The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores:
The National Cyber Security Division (NCSD) is a division of the Office of Cyber Security & Communications, within the United States Department of Homeland Security's Directorate for National Protection and Programs.
Cyber Storm, the Department of Homeland Security's (DHS) biennial exercise series, provides the framework for the most extensive government-sponsored cybersecurity exercise of its kind.
Homeland Security Presidential Directive 7: Critical Infrastructure Identification, Prioritization, and Protection
NIST: National Vulnerability Database.
Einstein is the product of U.S. congressional and presidential actions of the early 2000s including the E-Government Act of 2002 which sought to improve U.S. government services on the Internet. The software was developed by the United States Computer Emergency Readiness Team (US-CERT). The Privacy Act of 1974 does not apply to Einstein 2 data because its system of records generally do not contain personal information and so are not indexed or queried by the names of individual persons.
The National Infrastructure Advisory Council (NIAC) shall provide the President through the Secretary of Homeland Security with advice on the security of the critical infrastructure sectors and their information systems. The council is composed of a maximum of 30 members, appointed by the President from private industry, academia, and state and local government. Wiki
DHS partners with private sector security firms.
The book says it is clear that private business can do better than governmental orgaizations. Yet, it appears that both domains are needed.
ASIS International develops standards and guidelines to serve the needs of security practitioners in today's evolving and demanding global environment.
Privitization is on the rise....
The Ad Council's partnership on safety--Ads used to combat problems.
|
||
| Week 4 | |||
| Week 5 | Notes from class:
Domestic is what happens in the U.S. while international is what happens outside the U.S.
The Red Cross is a NGO.
When the NRF was written and thought through, it was realized that state and local agencies must work together with federal authorities. Thus, a grant system was set up whereby states can apply for money to be used to train, etc. for responsibilities for disasters.
In a pure democracy, 50 percent wins. A republic is a form of government in which the country is considered a "public matter" – not the private concern or property of the rulers – and where offices of state are elected or appointed, rather than inherited. It is a form of government under which the head of state is not a monarch. The Untied States is a republic.
The State, Local, Tribal, and Territorial Government Coordinating Council (SLTTGCC) strengthens the sector partnership structure by bringing together geographically diverse experts from a wide range of critical infrastructure disciplines to ensure that state, local, tribal, and territorial officials play an integral role in national critical infrastructure security and resilience efforts. This is a coordinating council--how do we talk to one another? other communications?
The Cabinet's role is to advise the President on any subject he may require relating to the duties of each member's respective office. It includes the president, vice president and all the secretaries along with other key parties such as the chief of staff, etc.
The fusion center reacts to criminal and police matters and NOT natural disasters.
The fusion center has classified information.
The government runs on the fiscal budget that begins October 1 until September 30.
A photograph of the Senate Appropriations Committee Room The Appropriations Committee reviews budget requests from the president, solicits testimony from government officials, and drafts funding legislation that gets reported to the full Senate. The Senate then works with the House to pass all appropriations bills by October 1, the beginning of the fiscal year.
The Department of Defense was once called the Department of War.
It is blurry the relationship between Homeland Security and Homeland Defense.
The Coast Guard is under the Navy in war and if not federalized, the National Guard is a state entity. Thus, thier authority may shift depending on the current state of the nation.
Assitiant Secretaries are VERY powerful.
The USNS Mercy ship is a hospital ship
Another ship, the comfort ship:
|
||
| Week 6 | |||
| Week 7 | |||
| Week 8 | |||
| Week 9 |
|
||
| Week 10 | |||
| Week 11 | |||
| Week 12 | |||
| Week 13 | |||
| Week 14 | |||